Connect two or more Azure Virtual Networks using one VPN Gateway
Peering is a feature that allows to connect two or more virtual networks and act as one bigger network. At this post we will see how we can connect two Azure Virtual Networks, using peering and access the whole network using one VPN Gateway. We can connect Virtual Networks despite if they are in the same Subscription or not.
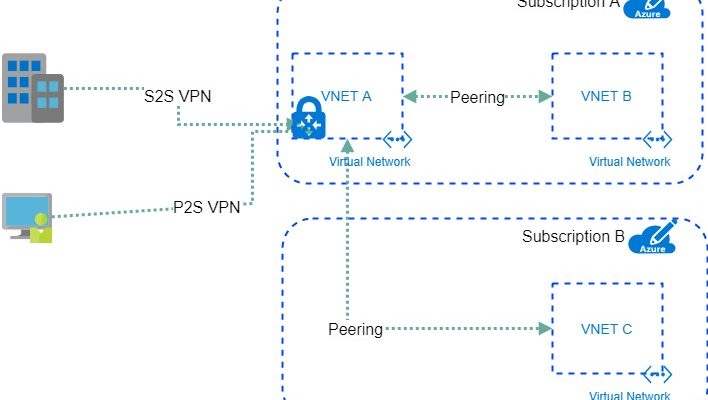
I have created a diagram to help understand the topology.

- We have a Virtual Network with Site-2-Site VPN wto On Premises. It can also have Point-2-Site connection configured. The VNET A.
- We have another Virtual Network at the Same Subscription that we want to connect each other. The VNET B.
- Also we can have a third Virtual Network at a different subscription. The VNET C.
In sort we need those peerings with the specific settings:
- At the VNETA Peering VNETA to VNETB with “Allow Gateway transit”
- At the VNETA Peering VNETA to VNET
- At the VNETB Peering VNETB to VNETA with “Use Remote Gateway”
- At the VNETB Peering VNETB to VNETC
- At the VNETC Peering VNETC to VNETA with “Use Remote Gateway”
- At the VNETC Peering VNETC to VNETB
In order to be able to connect all those networks and also access them using the VPN Connection there are four requirements:
- The account that will be used to create the peering must have the “Network Contributor” Role.
- The Address Space must be different on each other and not overlap.
- All other Virtual Networks, except the one that has the VPN Connection must NOT have a VPN Gateway deployed.
- Of course at the local VPN device (router) we need to add the address spaces of all the Virtual Networks that we need to access.
Lets lab it:
- HQ 192.168.0.0/16 –> The on-premises network
- VNET A 10.1.0.0/16 –> The Virtual Network that has the VPN Gateway (At my lab is named “devvn”)
- VNET B 10.229.128.0/24 –> THe virtual network at a different subscription of the Gateway (At my lab is named “Network prtg-rsg-vnet”)
- VNET C 172.16.1.0/24 –> The virtual network at the same subscription as the Gateway Network (At my lab is named “provsevnet)
The on-premises network is connected with Site-to-site (IPsec) VPN to the VNETA

Now we need to connect VNETA and VNETB using Vnet Peering. in order to have a Peering connection we need to create a connection from VNETA to VNETB and one from VNETB to VNETA.
Open the VNETA Virtual Network, go to the Peerings setting and press +ADD
Select the VNETB and check the “Allow Gateway transit” to allow the peer virtual network to use your virtual network gateway


Then go to the VNETB, go to the Peerings setting and click +ADD.
Select the VNETA Virtual Network and check the “Use Remote Gateway” to use the peer’s virtual network gateway. This way the VNETB will use the VNETA’s Gateway.


Now we can contact the VNETB network from our on-premises network
a multi-ping screenshot:
- From 10.229.128.5 (VNETB) to 192.168.0.4 (on-premises) & the opposite
- From 10..1.2.4 (VNETA) to 10.229.128.5 (VNETB) & to 192.168.0.4 (on-premises)

The next step is to create a cross-subscription peering VNETA with VNETC
Open the VNETA and create a peering by selecting the VNETC from the other Subscription and check the “allow gateway transit”

Then go to the VNETC and create a peer with the VNETA and check the “use remote gaeway”

With the two above connections we have connectivity between the on-premises network and the VNETC.
The final step, to enable the connectivity between VNETB & VNETC. To accomplish this just create one peer from the VNETB to VNETC and one from VNETC to VNETB.
Ping inception:

In order to have client VPN connectivity to the whole network, create a Point-2-Site VPN at the VNETA. You can follow this guide: Azure Start Point | Point-to-Site VPN

Pantelis Apostolidis is a Sr. Specialist, Azure at Microsoft and a former Microsoft Azure MVP. For the last 20 years, Pantelis has been involved to major cloud projects in Greece and abroad, helping companies to adopt and deploy cloud technologies, driving business value. He is entitled to a lot of Microsoft Expert Certifications, demonstrating his proven experience in delivering high quality solutions. He is an author, blogger and he is acting as a spokesperson for conferences, workshops and webinars. He is also an active member of several communities as a moderator in azureheads.gr and autoexec.gr. Follow him on Twitter @papostolidis.

I did everything like in here and I can not reach network on premise from VNET B. Which is really strange since I can access VNET B from on premise network.